Server-based Web Programming
(1DV023/1DV523)
Lecture
Web Security


Licensed for this work
This work is produced by John Häggerud for the course Server-based Web Programming (1DV023) at Linnaeus University.
All content in this work excluding photographs, icons, picture of course literature and Linnaeus University logotype and symbol, is licensed under a

Creative Commons Attribution 4.0 International License.
You are free to
- copy and redistribute the material in any medium or format
- spread the whole or parts of the content
- show the whole or parts of the content publicly and digital
- convert the content to another format
- change the content
If you change the content do not use the photographs, icons, picture of the course literature or Linnaeus University logotype and symbol in your new work!
At all times you must give credit to: ”Linnaeus university – Server-based Web Programming (1DV023)” with the link https://coursepress.lnu.se/kurs/serverbaserad-webbprogrammering/ and to the Creative Common-license above.
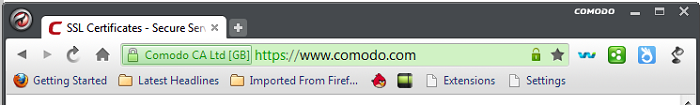
Low cost, just validate the domain
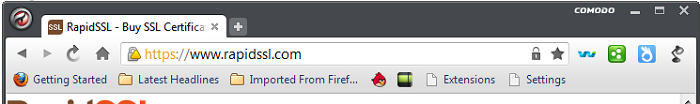
Organization Validation (OV)
Validates domain and the orgranization (addresses, country...)
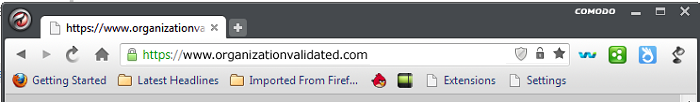
Extended Validation (EV)
Like OV plus more control of the organization that gives
higher thrust